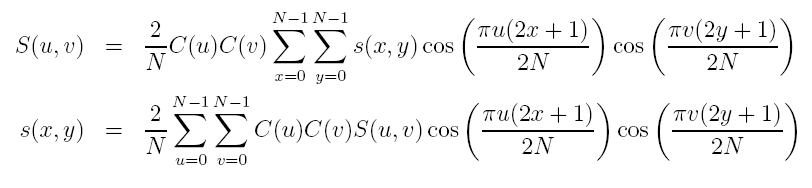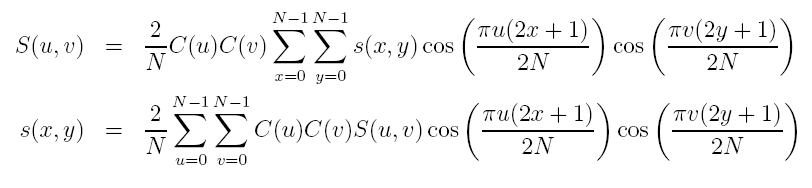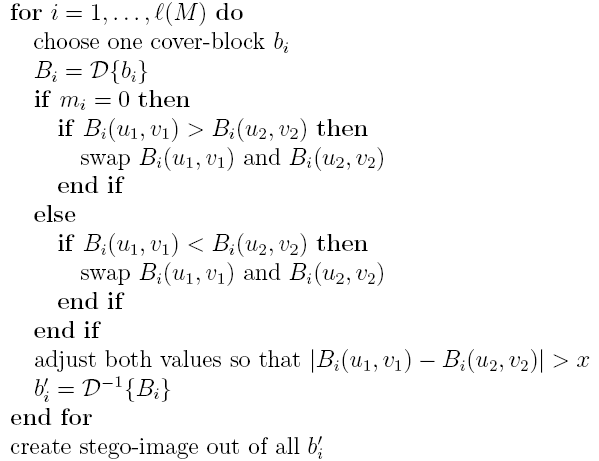Transfer Domain Techniques
The LSB method has the defect of being extremely vulnerable to even small cover
modifications. Transform domain methods hide messages in the significant areas
of the cover image.
There are many transform domain techniques, the most common being using the DCT. In digital
image processing the 2D DCT is usually used:
The basic way JPEG compression works is outlined below. The figure was obtained from [4].
In particular the influence of the highest DCT coefficients is reduced: they are usually
dominated by noise and not expected to contribute much to the picture details.
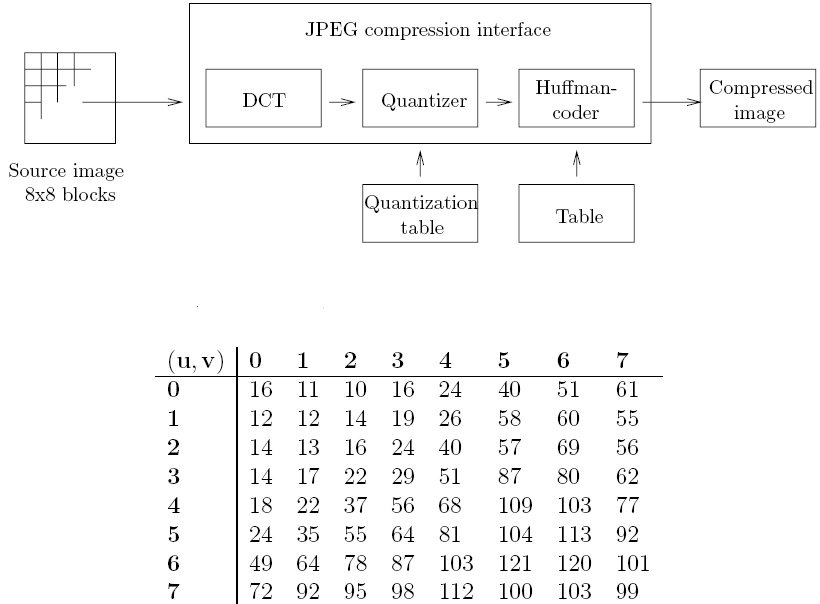 JPEG process outline & Quantization values used in JPEG
JPEG process outline & Quantization values used in JPEG
Having covered the basics, the popular way of doing steganography in the DCT domain is
to modulate the relative size of two or more DCT coefficients within
one image block.
The basic algorithm is described in [4] as splitting the image into 8x8 blocks and calculating
the DCT of the block. Then two middle-frequency (so that they are not to altered by the
quantization/compression which will take place in JPEG) are chosen and agreed upon by both
send and receive parties. A block encodes a 1 if DCT(a,b) > DCT(c,d) otherwise it encodes a 0.
In the encoding step the coefficients are swapped if their relative size does not match with
the bit to be encoded. Since the JPEG compression can affect the relative size of the coefficients
the algorithm ensures that abs(DCT(a,b) - DCT(c,d)) > x where x is a value which represents
the tradeoff between image quality and robustness.
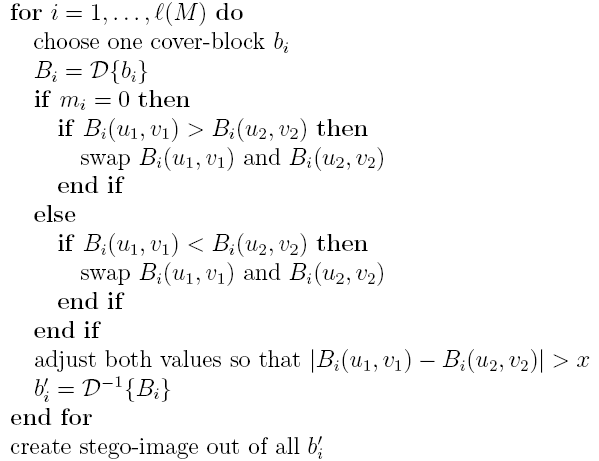 DCT Steganographic encoding
DCT Steganographic encoding
Decoding is straightforward in that all available blocks are DCT-transformed and by comparing
the coefficients of each block the information is restored. This method is similar to the one suggested by Zhao & Koch[13]. The problem with the method
outlined above is that it does not discard the image blocks where the desired relation of
DCT coefficients cannot be enforced without severely damaging the image in the specific block
whereas Zhao & Koch suggest a similar approach (which I did not implement for this project)
but with modifications to overcome this problem;
Implementation
The implementation of the above algorithm was done in Matlab; see the source code listings.
An example of this is described below.
The following source image was taken and split in 8x8 blocks. In each block 1 bit of a
text message was stored.
 Source/Cover image
Source/Cover image
The message which is encoded is:
Theres saying in Tennessee--I know its in Texas--says,fool me once--shame on—shame on you.You fool me,you cant get fooled again
After the algorithm was applied the generated stego image is shown below:
 Resultant image (after embedding message)
Resultant image (after embedding message)
As one can see there is a very small difference between the images.
Some details: the dimensions of the TIFF file above were
the