
We call a steganographic system pure when it does not require prior exchange of data like shared-keys. The
definition can be mathematically described[4] as
The set (C,M,D,E) where C is the set of covers, M the set of messages with |M| <= |C|, E the embedding function
which maps E:C x M -> C and D is the extracting function which maps from D:C -> M and the
property D(E(c,m))= m for all (m E M, c E C) is a pure steganographic system
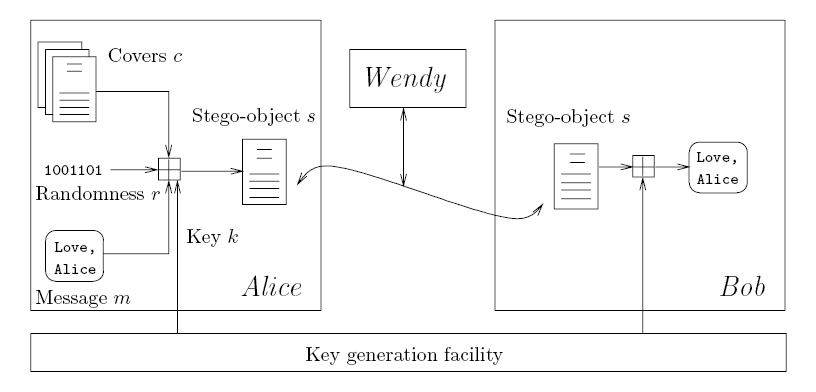
We call a steganographic system a shared-secret or shared-key or secret when it does not require prior exchange of data like shared-keys. The
definition can be mathematically described[4] as
The set (C,M,S,Ds,Es) where C is the set of covers, M the set of messages with |M| <= |C|, e the embedding function
which maps C x M -> C and S is the set of shared-secrets; Ds: C x S -> M and
Es: C x M x S -> C and the property Ds( Es(c,m,s) , s) = m for all (c E C, m E M, s E S) holds
is called a shared-secret steganographic system
This kind of steganography does not rely on shared-key exchange. Instead it is based on the public-key
cryptography principle in which there are two keys, one being the public key which can be usually obtained
from a public database and the other a private key. Usually in this case the public key is used in
the embedding process and the private key in the decoding process.
